Reputation Data Processing Addendum
1. Introduction
This Data Processing Addendum (the “Addendum”) is incorporated into the Order Form and Service Agreement (the “Agreement”) and applies in respect of the provision of the Services to the Customer if the Customer is subject to the European Data Protection Laws and the Company Processes Personal Data in connection with the Service. This Addendum shall be effective for the term of the Agreement.
2. Definitions
2.1 For the purposes of the Addendum:
- “Agreement” means the Service Agreement and Order Form;
- “Customer Personal Data” means Personal Data submitted, stored, uploaded or otherwise provided by Customer through its use of the Services, as further described under Section 3 of this Addendum;
- “EEA” means the European Economic Area;
- “European Data Protection Laws” means the GDPR, the UK GDPR and, to the extent applicable, the UK Data Protection Act 2018 (“DPA 2018”), in each case as amended, repealed, consolidated or replaced from time to time;
- “EU Controller to Processor Clauses” means the Module Two Clauses to the EU SCCs.
- “EU Standard Contractual Clauses” or “EU SCCs” means the standard contractual clauses for the transfer of personal data to third countries pursuant to Regulation (EU) 2016/679 of the European Parliament and the Council approved by the European Commission implementing decision (EU) 2021/914 of 4 June 2021.
- “GDPR” means the General Data Protection Regulation (EU) 2016/679; and
- “Personal Data”, “Data Subject”, “Data Protection Authority”, “Data Protection Impact Assessment”, “Personal Data Breach”, “Process”, “Processor” and “Controller” will each have the meaning given to them in the European Data Protection Laws.
- “UK Addendum” means the International Data Transfer Addendum to the SCCs issued by Information Commissioners Office under S.119(A) of the UK DPA 2018, as it is revised under Section 18 therein.
- “UK GDPR” means the GDPR as it forms part of the law of England and Wales, Scotland and Northern Ireland by virtue of section 3 of the European Union (Withdrawal) Act 2019.
2.2 Capitalized terms not otherwise defined herein shall have the meaning given to them in the Agreement.
3. Details Of The Processing
3.1 Categories of Data Subjects. This Addendum applies to the Processing of Customer Personal Data relating to Customer’s customers or patients or prospects and other end users, the extent of which is determined and controlled by Customer in its sole discretion.
3.2 Types of Personal Data. Customer Personal Data includes the following types of Personal Data: names, title, position, contact information (including email addresses and phone numbers), purchase or services information, and any other Personal Data, provided to the Company by the Customer.
3.3 Subject-Matter and Nature of the Processing. The subject-matter of Processing of Customer Personal Data by Company is the provision of the Services to the Customer. Customer Personal Data will be subject to those Processing activities which Company needs to perform in order to provide the Services pursuant to the Agreement.
3.4 Purpose of the Processing. Customer Personal Data will be Processed by Company for purposes of providing the Services set out in the Agreement.
3.5 Duration of the Processing. Customer Personal Data will be Processed for the duration of the Agreement, subject to Section 11 of this Addendum.
3.6 Frequency of the Transfer. Continuous.
4. Processing Of Customer Personal Data
4.1 Each of the Customer and the Company will comply with their respective obligations under the European Data Protection Laws, to the extent applicable to the Processing of any Customer Personal Data in the context of the provision of the Services.
4.2 Company will only Process Customer Personal Data as a Processor on behalf of and in accordance with the Customer’s prior written instructions and for no other purpose. Company is hereby instructed to Process Customer Personal Data to the extent necessary to enable Company to provide the Services in accordance with the Agreement.
4.3 If for any reason (including a change in applicable law) Company becomes unable to comply with any instructions of the Customer regarding the Processing of Customer Personal Data, Company will promptly:
- notify the Customer of such inability, providing a reasonable level of detail as to the instructions with which it cannot comply and the reasons why it cannot comply, to the greatest extent permitted by applicable law; and
- cease all Processing of the affected Customer Personal Data (other than merely storing and maintaining the security of the affected Customer Personal Data) until such time as the Customer issues new instructions with which Company is able to comply (and if this provision applies, Company will not be liable to the Customer under the Agreement in respect of any inability to perform the Services until such time as the Customer issues new instructions).
4.4 The parties agree that the Company’s reputation management SaaS platform used to perform the services under this Agreement (the “Platform”) shall be physically hosted within the EEA or the US.
4.5 The Company will, at Customer’s request provide the Customer with all information necessary to enable the Customer to demonstrate compliance with its obligations under the European Data Protection Laws, and allow for and contribute to audits, including inspections, conducted by the Customer or an auditor mandated by the Customer, to the extent that such information is within Company’s control and Company is not precluded from disclosing it by applicable law, a duty of confidentiality, or any other obligation owed to a third party. Company shall immediately inform the Customer if, in its opinion, an instruction infringes the European Data Protection Laws.
5. Confidentiality
5.1 Company will ensure that any person whom Company authorises to Process Customer Personal Data on its behalf is subject to confidentiality obligations in respect of that Customer Personal Data.
6. Security Measures
6.1 Company will implement appropriate technical and organisational measures to protect against accidental or unlawful destruction, loss, alteration, unauthorised disclosure of, or access to Customer Personal Data, as set out in Schedule 1.
7. Appointment of Subprocessors
7.1 Customer authorises Company to appoint Subprocessors to perform specific services on Company’s behalf which may require such Subprocessors to process Customer Personal Data. A current list of the Company Subprocessors may be found on the Reputation Subprocessors page. Customer acknowledges and agrees to the engagement of the third parties listed on the Subprocessor Page as Subprocessors in connection with the provision of the Services under this Agreement.
Where Company engages a Subprocessor, Company will enter into a Data Processing Agreement with the Subprocessor that imposes on the Subprocessor at least the same level of protections that apply to Company under this DPA. Where a Subprocessor fails to fulfill its data protection obligations, Company will remain liable to the Customer for the performance of such Subprocessor’s obligations.
7.2 Notification of New Subprocessors. If the Company retains new Subprocessors other than the companies listed on the Subprocessor Page, the Company will notify the Customer by updating the Subprocessor Page and will give the Customer the opportunity to object to the engagement of the new Subrocessors within 15 days after being notified. The objection must be based on reasonable legal grounds. If the Company and Customer are unable to resolve such objection, then either party may terminate the Agreement by providing written notice to the other party. If a Customer terminates, then Customer shall receive a refund of any prepaid but unused fees for the period following the effective date of termination.
8. Data Subject Rights
8.1 Company will, at the Customer’s request and subject to the Customer paying all of Company’s fees at prevailing rates, and all expenses, provide the Customer with assistance necessary for the fulfilment of the Customer’s obligation to respond to requests for the exercise of Data Subjects’ rights. Customer shall be solely responsible for responding to such requests.
9. Security Breaches
9.1 Company will:
- notify the Customer as soon as practicable after it becomes aware of any Personal Data Breach affecting, any Customer Personal Data; and
- at the Customer’s request and promptly provide the Customer with all reasonable assistance necessary to enable the Customer to notify a Personal Data Breach to the relevant Data Protection Authorities and/or affected Data Subjects.
10. Data Protection Impact Assessment; Prior Consultation
10.1 Company will, at the Customer’s request provide the Customer with reasonable assistance to facilitate:
- conducting of Data Protection Impact Assessments if the Customer is required to do so under the European Data Protection Laws; and
- consultation with Data Protection Authorities, if the Customer is required to engage in consultation under the European Data Protection Laws,
in each case solely to the extent that such assistance is necessary and relates to the Processing by the Company of the Customer Personal Data, taking into account the nature of the Processing and the information available to the Processor.
11. Return or Deletion of Customer Personal Data
11.1 Company will permanently and securely delete (or, at the election of the Customer, return, in such format as Company may reasonably elect and subject to the Customer paying all of Company’s fees at prevailing rates, and all expenses, for transferring the Customer Personal Data to such format) all Customer Personal Data in the possession or control of Company or any of its sub-Processors, within ninety (90) days after Company ceases to provide the Services, unless the applicable law of the EEA or EEA Member State or the UK requires otherwise. Company will procure that its sub-Processors do likewise.
12. Personal Data Transfers
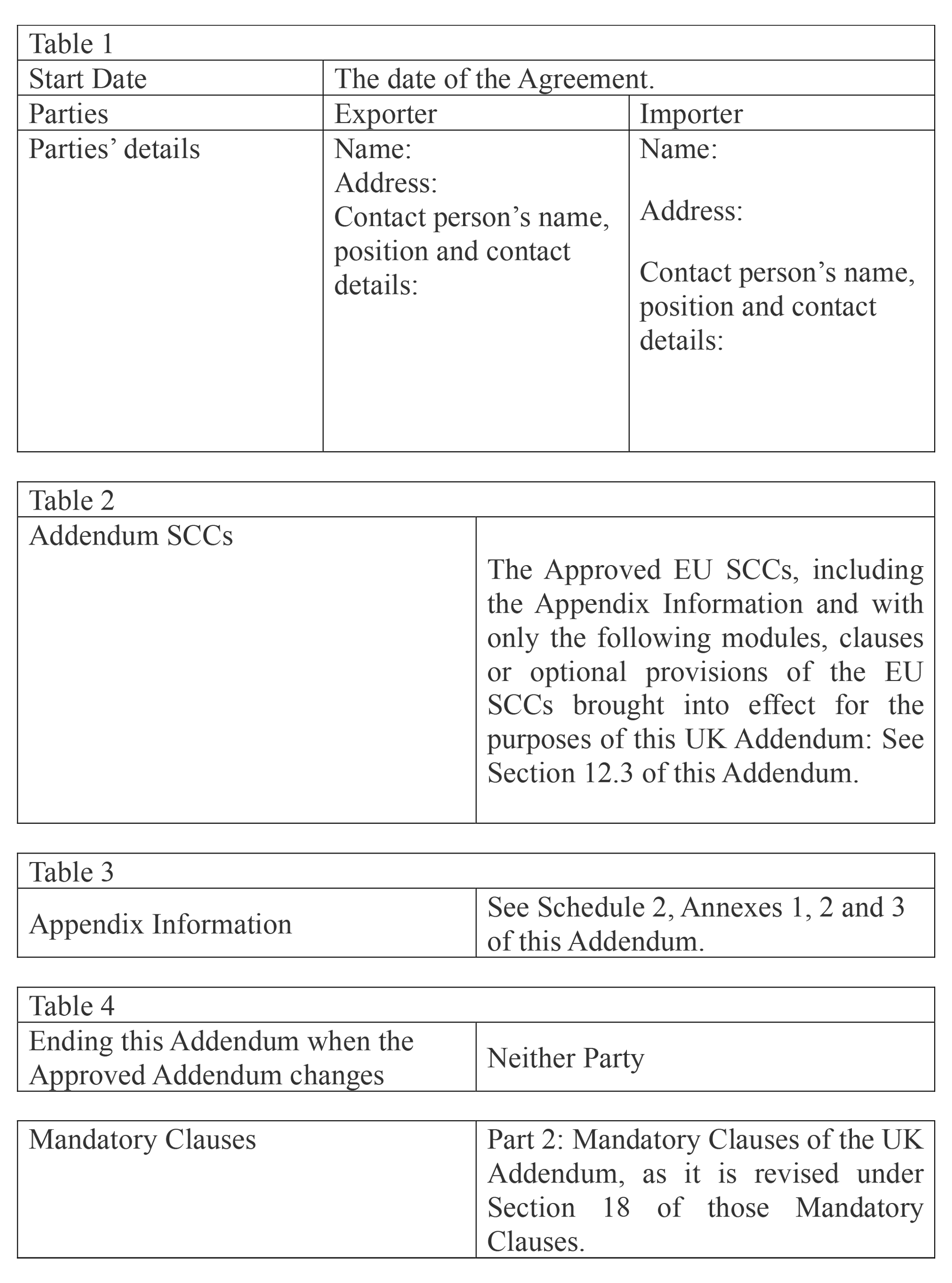
12.1 In connection with its provision of the Services, Company may transfer Customer Personal Data outside of the EEA and/ or the UK, including to its parent Reputation.com, Inc. and Subprocessors based outside the EEA and/ or the UK. Where the Company transfers Customer Personal Data outside of the EEA and/ or the UK to a country that is not deemed ‘adequate’ under European Data Protection Laws or does not offer other safeguards (for example binding corporate rules) compliant with European Data Protection Laws, the parties agree that the EU Controller to Processor Clauses shall apply, and/ or, as applicable, the UK Addendum attached as Schedule 3. Such EU SCCs and/ or the UK Addendum are hereby incorporated by reference into this Addendum.
12.2 Signature by Customer of an Order Form shall be deemed as signature of the EU SCCs.
12.3 With regard to the EU SCCs, the parties agree the following:
- 12.3.1 The requirements of the Appendix to the EU SCCs are as set out at Schedule 2.
- 12.3.2 The optional docking clause in Clause 7 shall not apply.
- Option 2 under Clause 9 shall apply. The data importer shall notify the data exporter 30 days in advance of any intended changes (via addition or replacement) to the list of sub-processors.
- 12.3.4 in Clause 11, the optional language shall not apply;
- 12.3.5 For the purposes of Clauses 13(a):
- 12.3.6 where the data exporter is established in an EU Member State: The supervisory authority with responsibility for ensuring compliance by the data exporter with Regulation (EU) 2016/679 as regards the data transfer will be Germany and shall act as competent supervisory authority.
- 12.3.7 For the purposes of Clause 17, the EU SCC’s shall be governed by German law;
- 12.3.8 For the purposes of Clause 18(b), disputes will be resolved before the courts of Germany.
12.4 To the extent of any conflict with the terms of this Addendum and the terms of the EU SCC’s and/ or the UK Addendum entered into by the parties, the terms of the applicable EU SCC’s or the applicable UK Addendum shall take precedence.
12.5 Where the Customer is not established in the EU, this Addendum shall be governed by the laws of England and the parties hereby submit to the exclusive jurisdiction of the English courts.
Schedule 1
Reputation.com Technical and Organizational Measures
Reputation.com and all of its affiliates (“Reputation” or “Company”) place a very high importance on the security of its organization and all customer data. The following is an outline of the extensive Technical and Organizational Measures (“TOMs”) that Reputation undertakes to protect customers’ data and all personal data from unauthorized access or disclosure. More detailed information is available upon request.
Compliance Program. Reputation is SOC2 Type II compliant as attested by a third-party auditor and is HIPAA compliant to ensure all customer personal data and protected health information (PHI) are properly handled. Reputation will share the latest SOC2 Type II report and our HIPAA Business Associates Agreement upon request and under NDA.
Customer Data. The Company maintains stringent datastore specifications for all customer data and personal data. All customer data and personal data is encrypted at rest using the AES symmetric block cipher and data is encrypted in transit using TLS. The Company does not disclose or sell the data and personal data that you provide to Reputation about your customers. The Company uses the data you provide us about your customers only to provide your services and for no other purpose. The Company will never request or require the private encryption key from a customer to decrypt exported protected data.
Platform Secure. The Company’s proprietary SaaS reputation management platform (“Platform”) and all customer data are maintained on secure servers at Google Cloud Services in the United States. The Google cloud infrastructure has been designed and is managed in alignment with key security and best practices, including, but not limited to: ISO 27001, SOC 1/SSAE 16/ISAE 3402(formerly SAS70); SOC 2, SOC 3, PCI DSS Level 1, FedRAMP(SM), DIACAP, FISMA, ITAR, FIPS 140-2, CSA, and MPAA.
Personal Data is Encrypted at Rest. Personal Data is encrypted in the Platform using Advanced Encryptions Standard (AES) algorithms.
Data in Transit is encrypted. Data in Transit is enforced encrypted via TLS 1.2 cryptographic protocol.
Password Security. The Company securely encrypts passwords. Passwords are one-way encrypted using the bcrypt algorithm, with a random salt for each password. This means that only the original creator of the password knows its value. When passwords must be retrieved, public/private key encryption is used, with a key length of 4096 or greater. Access and retention of passwords are strongly controlled and logged. Password policy with a minimum of 8 characters with at least 1 upper, 1 lower, 1 numeric and 1 special character is required.
Penetration Testing. Penetration tests are conducted by an independent third-party assessor at least annually. Reputation will share the latest Penetration Test report upon request and under NDA.
No Sensitive Information Collected or Stored. The Company does not collect or store sensitive information such as racial or ethnic origin, political opinions, religious or philosophical beliefs, or trade union membership, genetic data, biometric data, data concerning health or data concerning a natural person’s sex life or sexual orientation. The Company also does not collect or store personal financial data, Social Security Numbers, National Insurance numbers, government-issued ID numbers.
Access Control. Reputation subscribes to least privilege access as a part of our access control and conducts quarterly audits of our accounts to validate this control. Physical access to Reputation locations is controlled by card access readers, monitored by security cameras and all guest access is logged and monitored.
Business Continuity and Disaster Recovery. The Company has a full Business Continuity Plan as well as a Disaster Recovery Plan. The Company maintains separate regions in our public cloud that are used for the purpose of disaster recovery with a full synchronization of platform data baked in. In addition, the Company maintains separate instances of our proprietary Platform in the United States and the European Union to ensure compliance with the General Data Protection Regulation (‘GDPR’). With this separation, no personal data will ever leave the geographical region a customer has been assigned.
Threat Protection. The Company deploys the latest in threat detection/threat protection and monitors its infrastructure and application on a continuous basis for anomalous behavior and attacks. Additionally, the Company has built security into the SDLC and perform Application Security Testing on its code.
Security Breach Reporting. The Company has a formal Incident Response Plan which is maintained and reviewed on an annual basis. The Company has a process in place to quickly notify Customer of any security incidents involving personal data when a material incident is confirmed. The Company will provide Customer with reasonable assistance necessary to help meet GDPR obligations.
Security Awareness Training. All employees undergo training on security in the workplace as well as HIPAA training. Awareness education on security and data privacy topics are provided to employees on an ongoing basis. Employees must also renew the completion of Security Awareness training modules annually as well as adhere to our information security policies including our Information Security Policy as well as our Data Security Policy and Customer Confidentiality Policy.
Background Checks. All offers of employment at Reputation are contingent on the completion of a background screening and reference check. Employees and contractors must sign a confidentiality agreement and an agreement to abide by Company security policies and procedures.
Customer Personal Data Deletion Practices. Customer’s personal data is securely stored in the Platform only. Customer’s personal data is stored only for the duration of the Customer’s engagement with the Company. The Company permanently and securely deletes all customer’s personal data in the possession or control of Company or any of its sub-processors, provided that Company has no legal obligation to maintain that data, within 90 days after (i) Company ceases to provide the services to Customer or (ii) the Customer has instructed the Company to delete any customer’s personal data. Company shall also procure that its sub-Processors do likewise.
Schedule 2: Appendix to the EU SCCs
APPENDIX
EXPLANATORY NOTE:
It must be possible to clearly distinguish the information applicable to each transfer or category of transfers and, in this regard, to determine the respective role(s) of the Parties as data exporter(s) and/or data importer(s). This does not necessarily require completing and signing separate appendices for each transfer/category of transfers and/or contractual relationship, where this transparency can achieved through one appendix. However, where necessary to ensure sufficient clarity, separate appendices should be used.
ANNEX I
A. LIST OF PARTIES
- MODULE ONE: Transfer controller to controller
- MODULE TWO: Transfer controller to processor
- MODULE THREE: Transfer processor to processor
- MODULE FOUR: Transfer processor to controller
Data exporter(s):
[Identity and contact details of the data exporter(s) and, where applicable, of its/their data protection officer and/or representative in the European Union]
- Name: …As described in the Agreement.
- Address: …As described in the Agreement
- Contact person’s name, position and contact details: …As described in the Agreement
- Activities relevant to the data transferred under these Clauses: …As described in the Agreement
- Signature and date: …
- Role (controller/processor): …Controller
Data importer(s):
[Identity and contact details of the data importer(s), including any contact person with responsibility for data protection]
- Name: …Reputation.com, Inc or Reputation.com (UK) Limited as detailed in the Agreement
- Address: …
- Contact person’s name, position and contact details: …legalnotices@reputation.com
- Activities relevant to the data transferred under these Clauses: …As described in the Agreement
- Signature and date: …
- Role (controller/processor): …Processor
B. DESCRIPTION OF TRANSFER
- MODULE ONE: Transfer controller to controller
- MODULE TWO: Transfer controller to processor
- MODULE THREE: Transfer processor to processor
- MODULE FOUR: Transfer processor to controller
Categories of data subjects whose personal data is transferred
- As set out in section 3.1
Categories of personal data transferred
- As set out in section 3.2
Sensitive data transferred (if applicable) and applied restrictions or safeguards that fully take into consideration the nature of the data and the risks involved, such as for instance strict purpose limitation, access restrictions (including access only for staff having followed specialised training), keeping a record of access to the data, restrictions for onward transfers or additional security measures.
- As set out in section 3.2
The frequency of the transfer (e.g. whether the data is transferred on a one-off or continuous basis).
- As set out in section 3.6 …
Nature of the processing
- As set out in section 3.3 …………………………
Purpose(s) of the data transfer and further processing
- As set out in section 3.4
The period for which the personal data will be retained, or, if that is not possible, the criteria used to determine that period
- As set out in section 3.5 ……………………..
For transfers to (sub-) processors, also specify subject matter, nature and duration of the processing
- As set out in section 3.3
C. COMPETENT SUPERVISORY AUTHORITY
- MODULE ONE: Transfer controller to controller
- MODULE TWO: Transfer controller to processor
- MODULE THREE: Transfer processor to processor
Identify the competent supervisory authority/ies in accordance with Clause 13
- As set out in section 12.3.6….
ANNEX II – TECHNICAL AND ORGANISATIONAL MEASURES INCLUDING TECHNICAL AND ORGANISATIONAL MEASURES TO ENSURE THE SECURITY OF THE DATA
MODULE ONE: Transfer controller to controller
MODULE TWO: Transfer controller to processor
MODULE THREE: Transfer processor to processor
EXPLANATORY NOTE:
The technical and organisational measures must be described in specific (and not generic) terms. See also the general comment on the first page of the Appendix, in particular on the need to clearly indicate which measures apply to each transfer/set of transfers.
Description of the technical and organisational measures implemented by the data importer(s) (including any relevant certifications) to ensure an appropriate level of security, taking into account the nature, scope, context and purpose of the processing, and the risks for the rights and freedoms of natural persons.
- As set out in Schedule 1
For transfers to (sub-) processors, also describe the specific technical and organisational measures to be taken by the (sub-) processor to be able to provide assistance to the controller and, for transfers from a processor to a sub-processor, to the data exporter
- As set out in Schedule 1
ANNEX III – LIST OF SUB-PROCESSORS (Not applicable – Option 2 selected)
- MODULE TWO: Transfer controller to processor
- MODULE THREE: Transfer processor to processor
EXPLANATORY NOTE:
This Annex must be completed for Modules Two and Three, in case of the specific authorisation of sub-processors (Clause 9(a), Option 1).
The controller has authorised the use of the following sub-processors:
- Name: …
- Address: …
- Contact person’s name, position and contact details: …
- Description of processing (including a clear delimitation of responsibilities in case several sub-processors are authorised):
Schedule 3: UK Addendum
This Schedule 3 forms part of this Addendum and applies in accordance with Section 12.1 of this Addendum.